I wrote this thread on Twitter in response to Charles Hoskinson’s YouTube videos Security Foundations: How to Secure Your Wallet Recovery Phrase for Cryptocurrency Wallets, Brief Comments on the Yubikey PGP Step (Security Foundations), and Surprise AMA 08/14/2020, in reference to an issue regarding instructions for backing up PGP keys using Kleopatra when generated via a YubiKey, within the broader topic of the Cardano blockchain and the ADA cryptocurrency. Since it took me some time to put together, I’m republishing it here.
I was curious after watching your video, so gave it a whirl on a (somewhat broken) YubiKey 5C, installing Kleopatra 3.1.8. (YubiKeys are nice, but mine hasn’t survived a year or two on my keyring what with running and rain…) I think the .gpg extension is a red herring; …
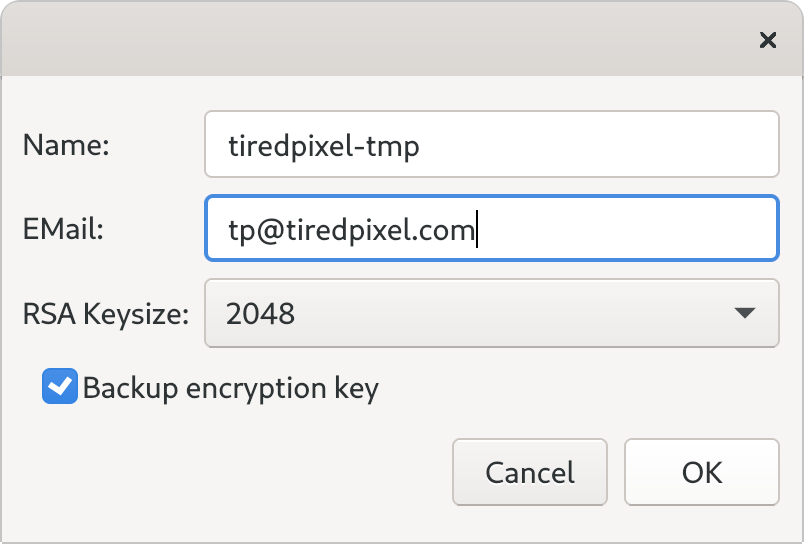
… it’s non-ASCII-armoured, rather than encrypted. I’ve seen both .asc and .gpg (and others like .key), regardless of whether it’s armoured or not. Generating the key shows the subkeys: sign/certify (SC), encryption (E), authentication (A). Since Kleopatra uses the GPG …
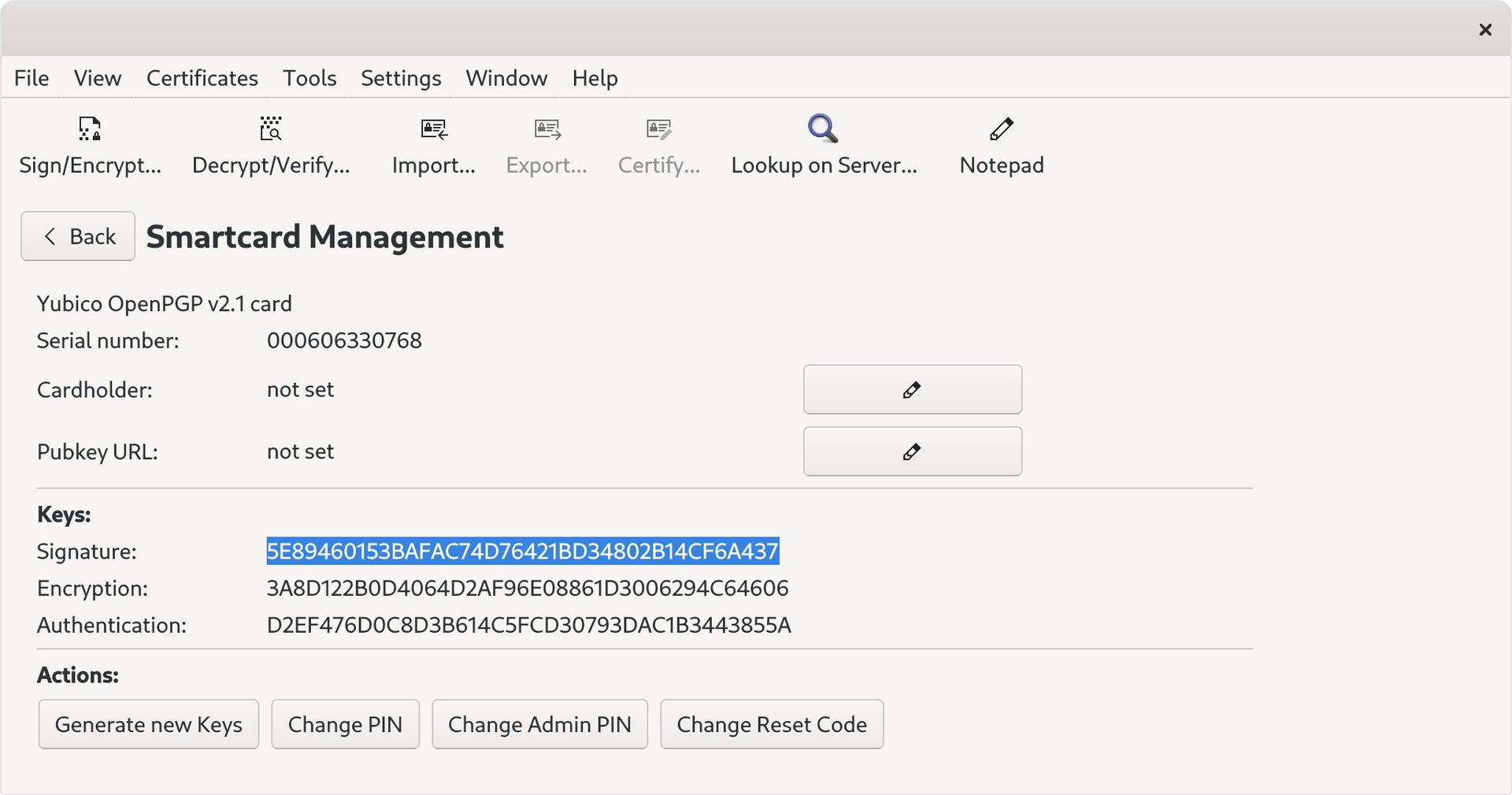
… keyring, we can use gpg CLI to check what’s going on. Here we can see the subkeys. The Kleopatra backup is named after the encryption (E) subkey ID. Attempting to use gpg --import fails with no user ID error. We export the E subkey, with -a to armour (note the !). …
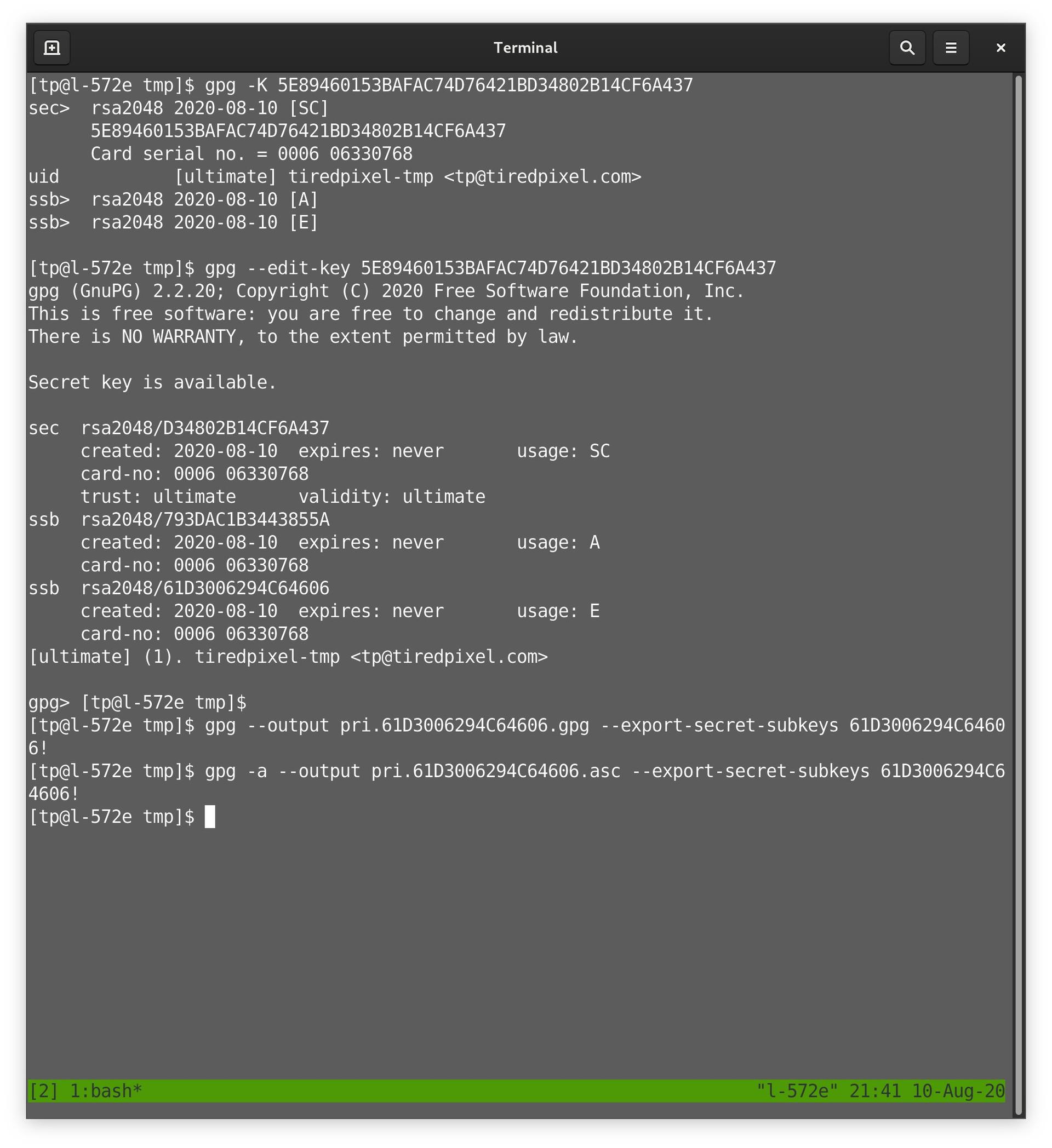
… We use gpg --list-packets to inspect the metadata. Diff shows us armoured and non-armoured metadata is the same. But comparing to Kleopatra backup, we see it doesn’t contain various parts, including the user ID. It’s an incomplete backup, even considering that subkey. …
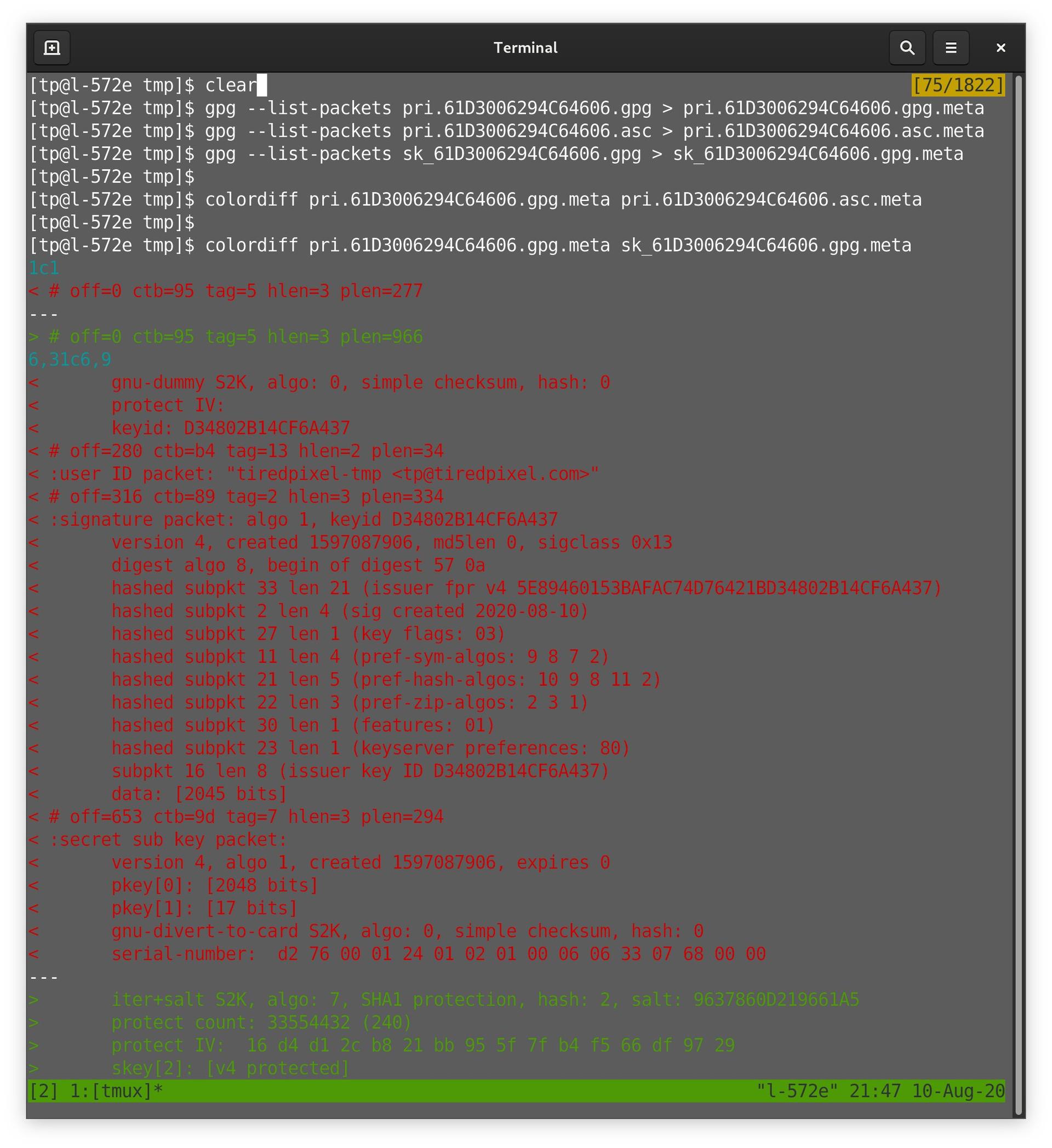
… But actually the aim is to have a fully-restorable backup. We export the full secret key, and see it contains extra parts, including the authentication (A) subkey. …
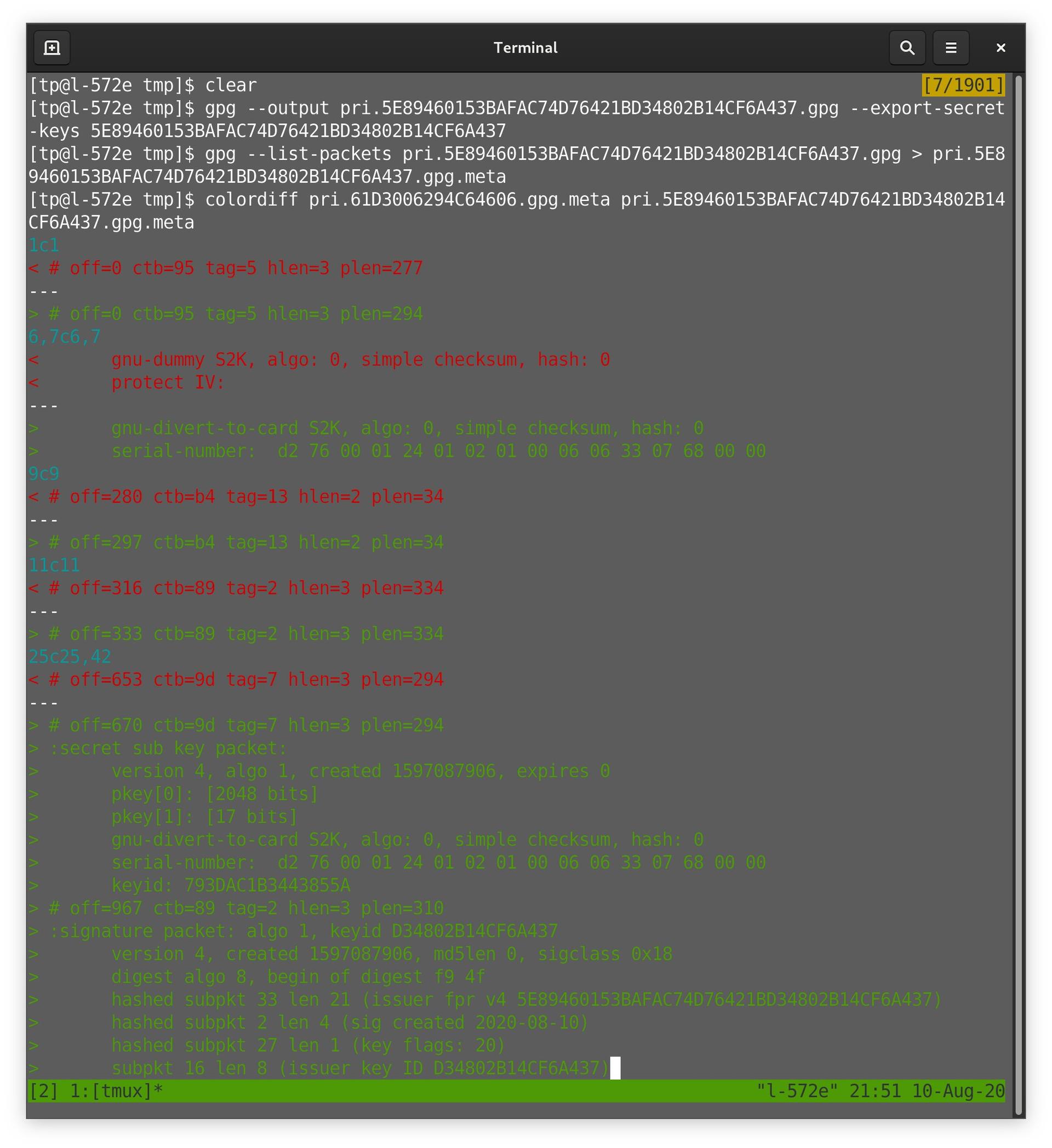
… Back to Kleopatra, we export the secret key directly from the interface, rather than just when generating the keys on the YubiKey. Remember that they’re actually stored in the keyring at this point. This file is different: .asc (doesn’t matter), and the full secret key. …
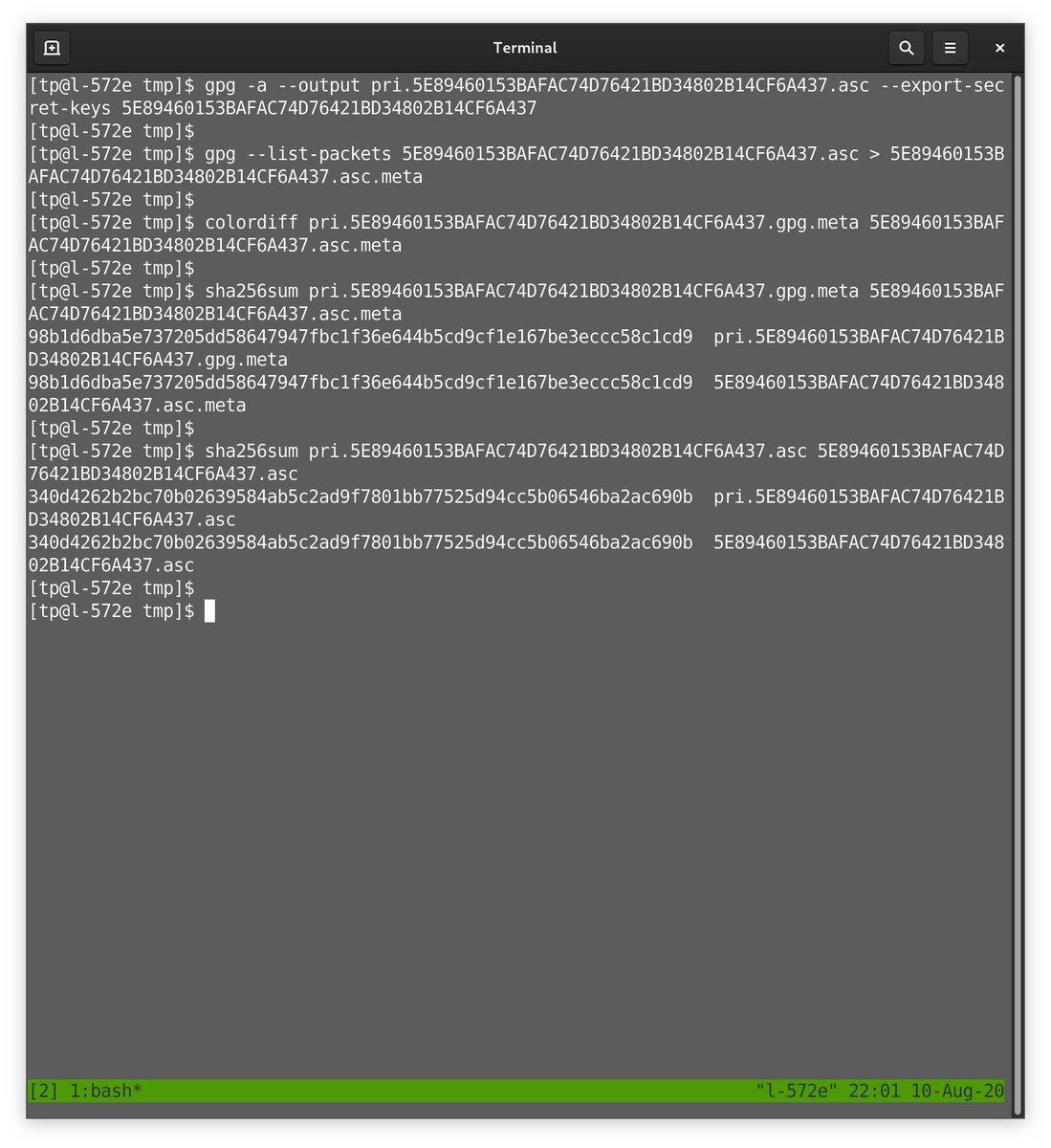
… We generate an armoured export of the secret key using gpg CLI, and list the packets. Diff shows again that the metadata is identical. However, checksums show that the CLI export matches the Kleopatra backup—it’s a full secret backup—and it’s armoured. …
… This should be restorable. As a side note, I’m not actually convinced by the double-encryption approach in the first video, but I haven’t gone through it or thought about it in detail. More common seems to be to split the subkey storage between the smart card etc., leaving …
… the master key as the ‘cold’ key, one or more subkeys as the ‘hot’ key. My thoughts are that this is fiendishly complicated for the average user, though, and likely to end in tears if attempted. As I say, I haven’t looked at it properly. ∎